Cyber resilience and cyber recovery are both critical components of a robust cybersecurity strategy but they address different aspects of managing and mitigating cyber threats. Though there has been a greater emphasis in the past on preventing cyber attacks from occurring, organizations and regulators alike are increasingly recognizing the importance of cyber recovery as it is impossible to guarantee that no breach will occur. Effective practices for cyber incident response and recovery are both necessary to ensure your organization is protected.
Let’s start by explaining what cyber resilience and cyber recovery are, their differences and how they are both essential for protecting organizations against the effects cyber attacks.
What is cyber resilience?
Cyber resilience is a holistic, proactive strategy that focuses on an organization's ability to anticipate, prepare for, respond to, and recover from cyber attacks. It involves not only preventing attacks but also ensuring that systems and processes can adapt and continue to function in the face of disruptions. Cyber resilience operations encompass a wide range of activities, including risk assessments, incident response planning, employee training, and the implementation of technologies that can detect and mitigate threats in real time. The goal of cyber resilience is to build an organization's capacity to withstand and recover quickly from cyber incidents while maintaining essential functions.
What is cyber recovery?
Cyber recovery specifically refers to a responsive solution involving the processes and measures put in place to restore and recover data, systems, and services after a cyber incident. It is a subset of cyber resilience, focusing on the restoration of critical technology assets that may have been compromised, damaged, or rendered inaccessible during an attack. Cyber recovery strategies are well-defined recovery procedures that include recovery from the last known good sources of data. The emphasis is on minimizing downtime and ensuring that the organization can return to normal operations as swiftly as possible.
While cyber resilience is a broader concept encompassing proactive measures to prevent, respond to, and recover from cyber threats, cyber recovery is a more narrowly focused aspect that deals specifically with recovering data and systems in the aftermath of a cyber incident. Both are crucial for ensuring the overall continuity of operations for modern organizations in an increasingly complex and dynamic cyber threat landscape.
What is the difference between cyber resilience and cyber recovery?
Ultimately, cyber resilience and cyber recovery make up two halves of ensuring your organization is protected against cyber threats. Cyber resilience is the defense while cyber recovery is the cure.
Cyber resilience encompasses:
- Building secure systems that make it harder for bad actors to penetrate your defenses
- Training teams to recognise cyber threats such as phishing emails to reduce the likelihood of a breach
- Proactively monitoring and updating cyber defenses to prevent attacks
However, no matter how advanced your cyber resilience strategies, there is always a chance that cyber attackers will get past your defenses. This is where cyber recovery comes in to:
- Restore systems and operations to the last known good source of data
- Minimize impacts and get back to business as usual
See the key differences between a cyber resilience strategy and the cyber recovery solution below:
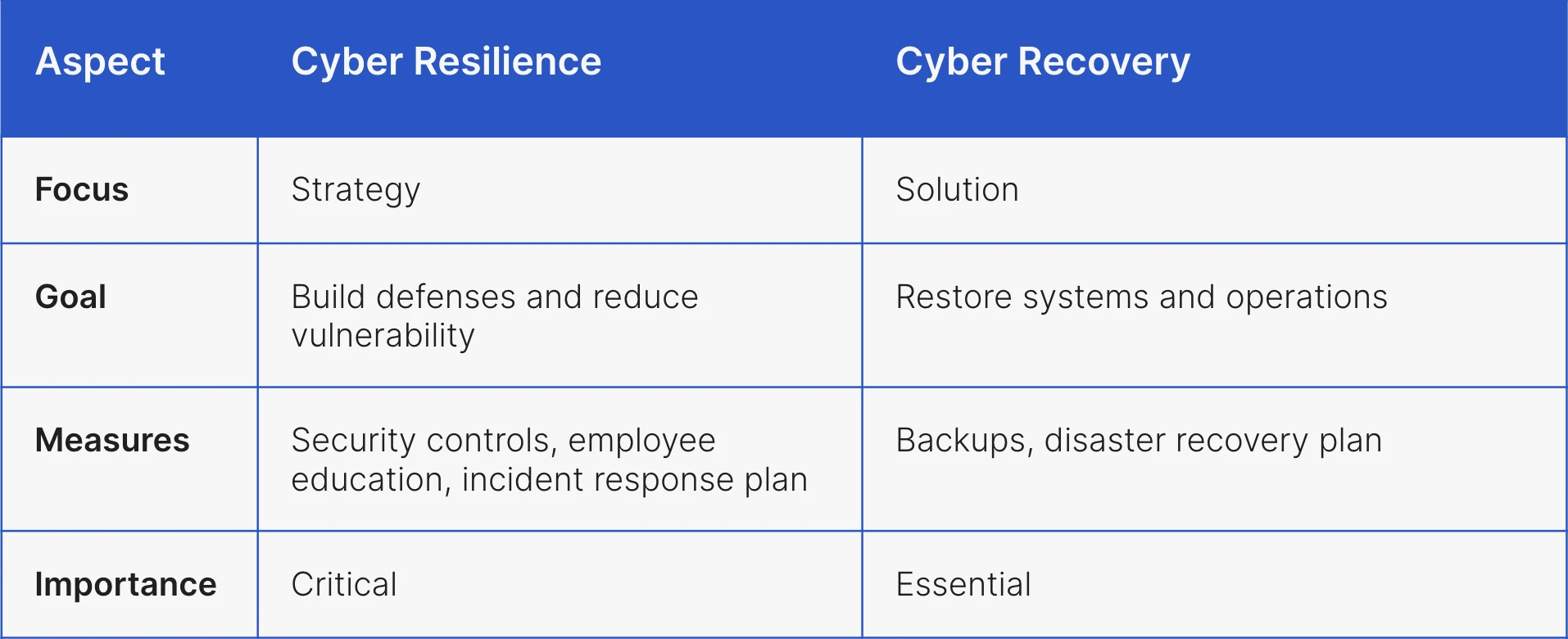
How Cutover can help you manage cyber recovery
Cutover’s cyber recovery solution provides a collaborative automation platform for teams to plan, orchestrate, and execute cyber recovery:
- Cutover can be used to develop and execute detailed cyber recovery plans. It allows organizations to define and automate the steps involved in responding to a cyber incident, ensuring a swift and coordinated reaction from relevant teams.
- Collaboration features in Cutover allow teams to communicate and collaborate in real time during the recovery process. This is crucial for coordinating activities, sharing updates, and managing tasks efficiently.
- Cutover’s automated runbooks orchestrate the complex sequence of tasks involved in cyber recovery, ensuring that teams and technology follow the set path in the correct order by automatically notifying people when to start their tasks and triggering automated processes. When orchestration is automated in the runbook, there is no need for a person to manually sequence the tasks or spend time letting teams know when they need to take action.
- Cutover can integrate with monitoring tools to provide real-time insights into the status of recovery activities. It can generate reports and dashboards to track progress, identify bottlenecks, and assess the overall effectiveness of the recovery process.
- The Cutover platform facilitates the creation of detailed documentation and audit trails for cyber recovery activities. This documentation is crucial for regulatory and compliance purposes and for analyzing the effectiveness of recovery efforts.
Cyber resilience and cyber recovery are both essential
Both cyber resilience and cyber recovery are crucial for protecting against increasing cyber threats to organizations. Proactive cyber resilience is needed to reduce the likelihood of cyber attackers successfully penetrating your defenses but the chances of this happening are never zero. This is why robust cyber recovery processes are also needed to ensure you can recover from an attack - and Cutover can help.
About Cutover
Cutover’s Collaborative Automation SaaS platform enables enterprises to simplify complexity, streamline work, and increase visibility. Cutover’s automated runbooks connect teams, technology, and systems, increasing efficiency and reducing risk in IT disaster and cyber recovery, cloud migration, release management, and technology implementation. Cutover is trusted by world-leading institutions, including the three largest US banks and three of the world’s five largest investment banks.
Book a demo to see the platform in action.
