As ransomware attack methods evolve, businesses face intensifying cyber threats that are projected to cost $265 billion annually by 2031. Cutover’s cyber recovery solution provides AI-powered, automated runbooks that allows organizations to transition from passive defense to an active, executable recovery posture.
Key challenges in modern cyber resilience
Modern organizations struggle with several critical barriers to cyber resilience:
- Escalating Threat Landscape: Cyber attacks are intensifying, forcing businesses to constantly rebalance security posture across data protection and corporate risk.
- Complexity of Execution: Recovering from a disaster requires an automated, executable plan to replace manual processes that fail during the pressure of a live event.
- Inconsistent Rehearsals: Without a single platform to store and test response plans, recovery strategies often become outdated and fail to reflect new attack vectors.
- Visibility Gaps: A lack of real-time control and centralized reference points makes it difficult for stakeholders to understand who is performing specific tasks during a crisis.
Cutover automated runbooks for cyber resilience
Cutover optimizes cyber recovery by providing a single platform to codify, orchestrate, and automate complex recovery processes.
- Dynamic Automated Runbooks: Cutover brings together automated and manual tasks into a multi-threaded task flow, reducing the time required to execute IT recovery.
- Seamless Integration: The platform integrates with existing toolsets like Ansible, Terraform, and ITSM platforms to quickly recover systems on bare-metal servers from air-gapped, immutable data.
- Real-Time Stakeholder Visibility: Centralized dashboards and automated communications via Slack, Teams, and Zoom ensure consistent updates across the business throughout a recovery event.
- Continuous Improvement and Compliance: Detailed audit trails and advanced analytics enable organizations to meet regulatory requirements, baseline RPOs, and iterate on strategies through post-event reviews.
What are the benefits of using Cutover for cyber recovery of IT applications?
Cutover’s automated recovery platform helps enterprises optimize recovery of cyber incidents, providing the following benefits.
Codify and rehearse the process to recover from a cyber incident
- Be prepared for unannounced cyber recovery simulations and live events
- Build detailed, dynamic automated runbooks that codify the cyber recovery process
- Rehearse incident recovery simulations for ransomware or system/application deletion
- Eliminate manual processes through automation to recover faster
- Rehearse both unannounced and planned resilience testing sequences
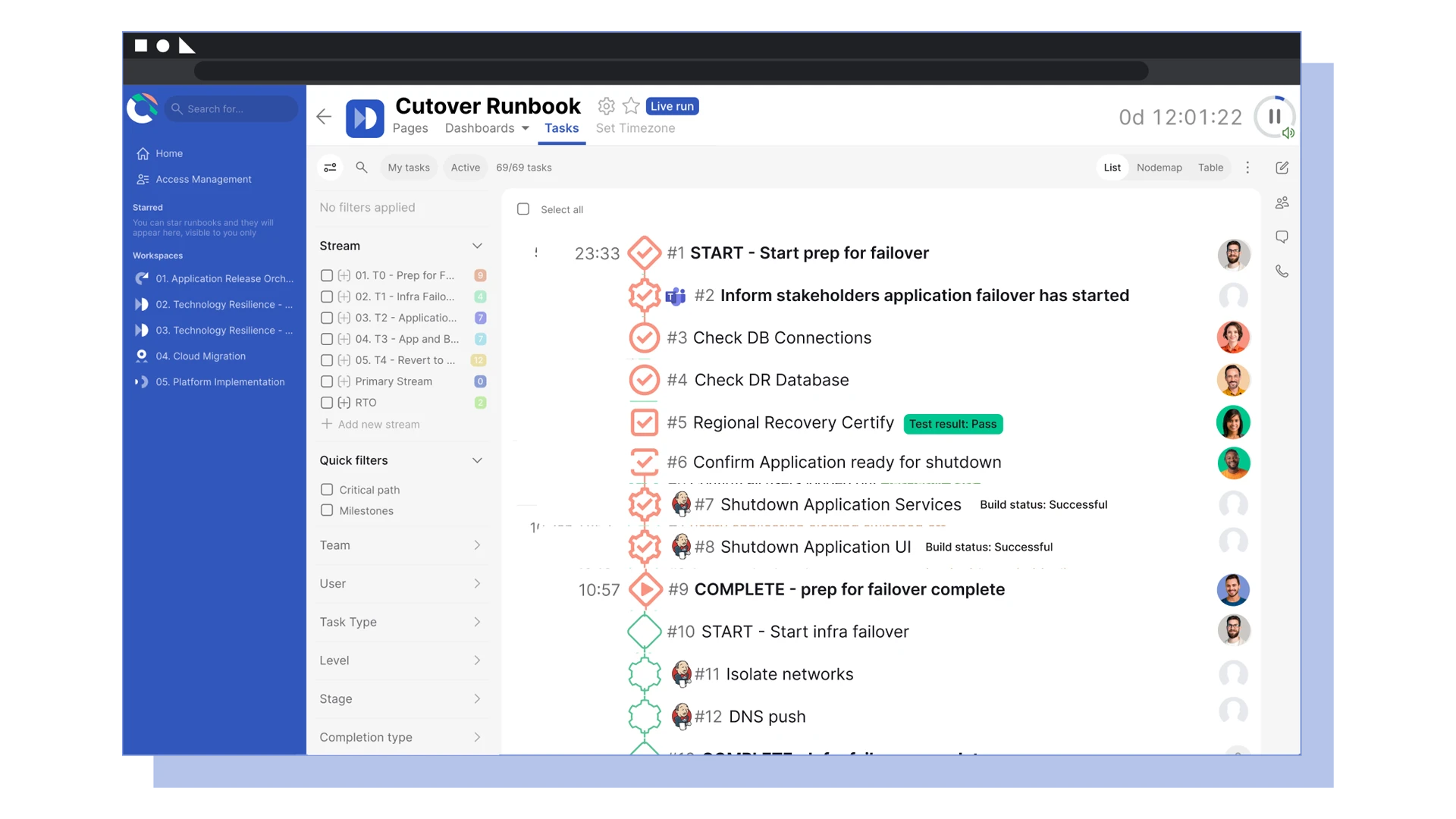
Collaborate efficiently across disaster recovery teams
- Successfully orchestrate the steps to recover from a ransomware attack and ensure recovery is from air-gapped and immutable data
- Execute and report in real time on disaster recovery rehearsals and live incidents
- Automate all manual tasks and integrate with existing tools to reduce the amount of time needed to take action in a crisis
- Integrate with your ITSM platform for golden source of systems configurations and governance data as well as tools such as Ansible or Terraform to quickly recover systems and applications on bare-metal servers
- Connect your recovery teams and technology to ensure efficient collaboration throughout rehearsals and live recovery incidents
- Ensure timely and consistent communications across the entire business with integrations to Slack, Microsoft Teams, Zoom, and more
- Inform stakeholders with real-time reporting on cyber recovery execution
Create a governance framework with visibility into real time analytics
- Ensure resolution service-level agreements (SLAs) and recovery time objectives (RTOs) for cybersecurity are met
- Baseline your recovery point objectives (RPOs) with air-gapped, immutable data and applications
- Easily meet and report on regulatory requirements with an indelible audit trail
- Regularly review and update cyber recovery strategies to reflect new risks and potential attack vectors
- Analyze, iterate, and audit your cyber resilience posture
- Conduct effective post-event reviews with detailed recovery information to optimize recovery plans and reduce risk
Cutover takes the risk and cost out of your cyber resilience operations by enabling better collaboration between teams and automation.







.webp)
