Cutover for cyber recovery
Save time and money on recovering from cyber attacks
Cyber attack methods constantly change as bad actors evolve and expand their techniques. All signals indicate the upcoming years will worsen as cyber attacks intensify while businesses attempt to balance the prioritization of their security defense posture across data protection, privacy, and overall corporate risk.
According to a 2022 Ransomware Market Report by Cybersecurity Ventures, ransomware alone will cost businesses around $265 billion (USD) annually by 2031. So, it’s not a matter of if you will experience a cyber attack, but when. To ensure you’re prepared for when bad actors penetrate your network defenses and a cyber recovery is required, you need automated and executable recovery runbooks in place.
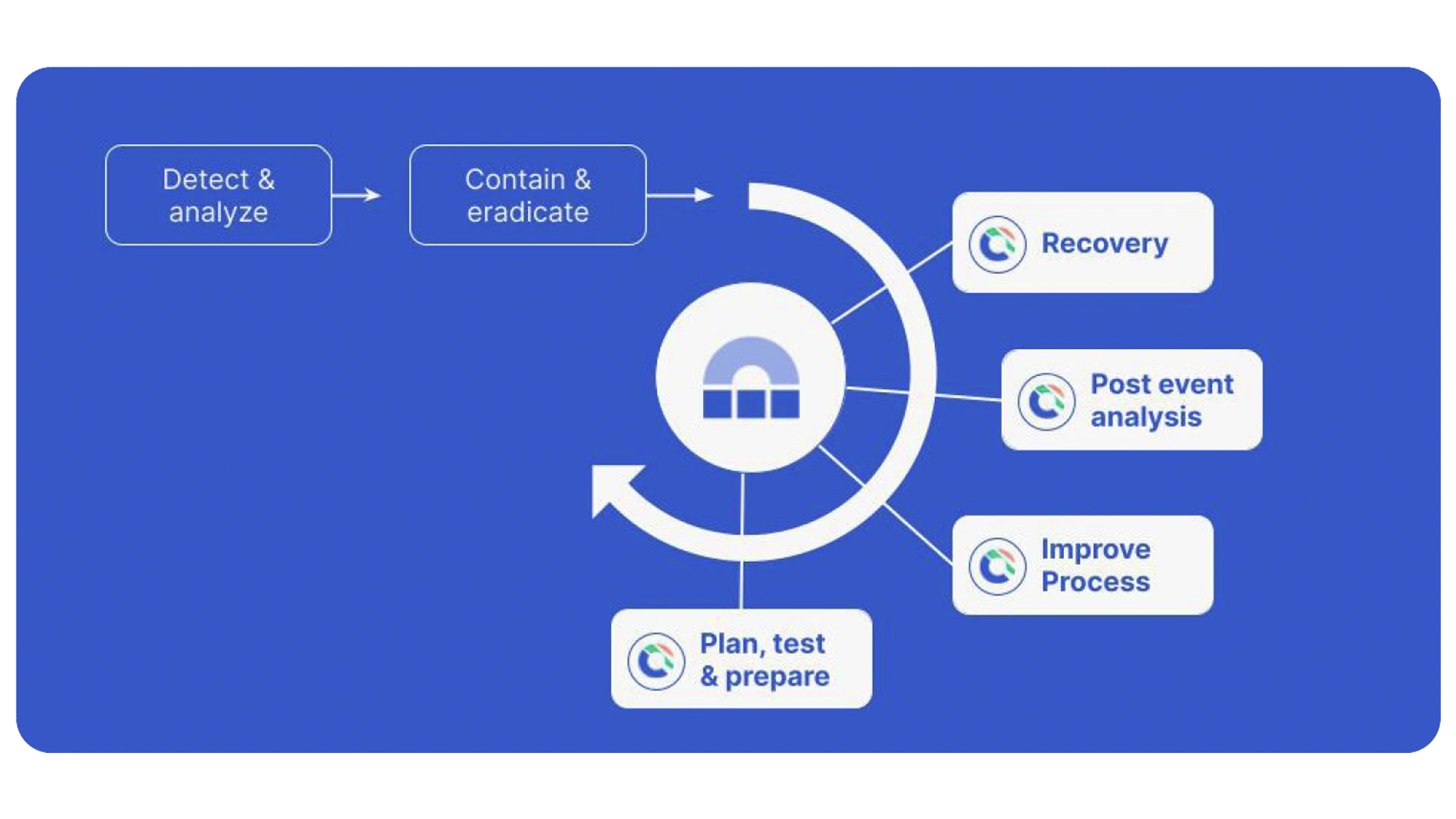
Cyber recoveries are at a level of complexity and unpredictability above standard IT outages. In the case of a ransomware attack, for example, you cannot easily understand the degree of the blast radius which makes recovering so unpredictable. Proper cyber recovery involves an orchestrated, multi-level set of runbooks as you need to recover across the access control plane, applications, services and air-gapped data. As cyber threats constantly evolve, recovery runbooks need to be regularly exercised and hardened for a strong security recovery posture.
Cutover provides a comprehensive and holistic approach to recovering from cyber incidents by automating repetitive tasks and workflows to free up your Security Operations Center (SOC) analysts for more strategic work in times of a business crisis.
As a result of using Cutover, IT and SOC teams can respond more quickly and effectively to security incidents in order to get the business back online while recovering from the cyber incident.
Cutover provides a single platform for all of your cyber recovery runbooks which brings together both automated and manual tasks. Cutover’s precision runbook orchestration provides consistency across your complex critical architectures and data, enabling you to reduce the time it takes to codify and execute cyber recovery processes and capture multi-threaded task flows so you can fully understand the sequence of activities across your recovery teams and supporting automation tools.
Cutover serves as the central point of execution and control thanks to real-time dashboards that provide visibility for business stakeholders throughout the process. All events and tasks are captured and automatically recorded by the Cutover platform, satisfying regulatory and compliance requirements with an immutable audit log. Finally, Cutover’s advanced analytics provide a clear picture of how your recovery performed so you can evaluate whether objectives were met, how effectively the program was executed and future actions required to make improvements.
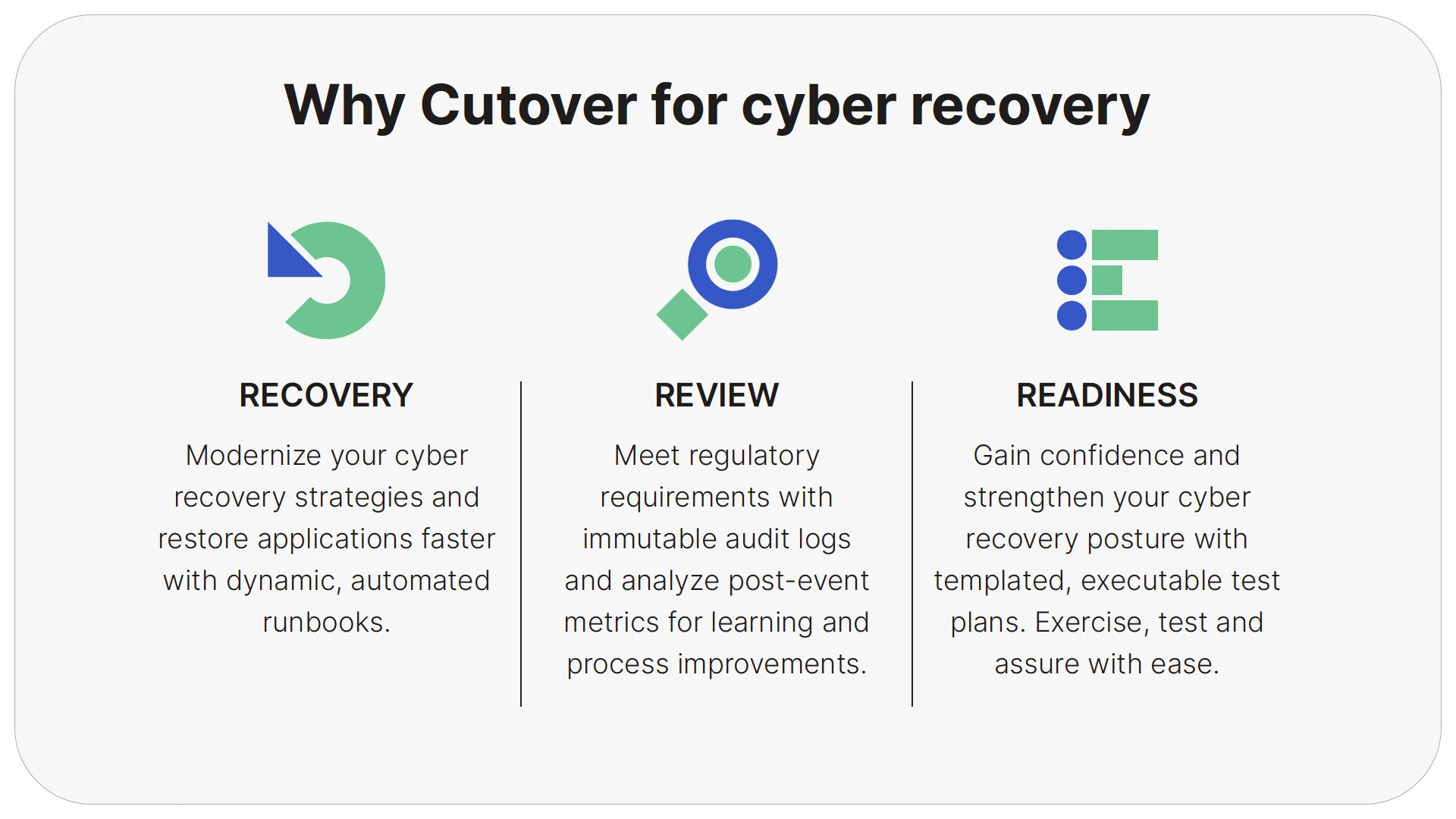
Cutover takes the risk and cost out of your cyber recovery operations by enabling better collaboration between teams and automation. Watch this video to learn more.







.webp)
